Hello, my ever-vigilant cyber sentinels! Today, we’re delving into a topic that’s guaranteed to make any CISO reach for the aspirin—insider threats. Now, I know what you’re thinking: “Isn’t it enough that we’re constantly battling external attackers, patching vulnerabilities, and keeping up with the latest cyber gizmos?” But here’s the kicker: some of the most…
Category: Articles
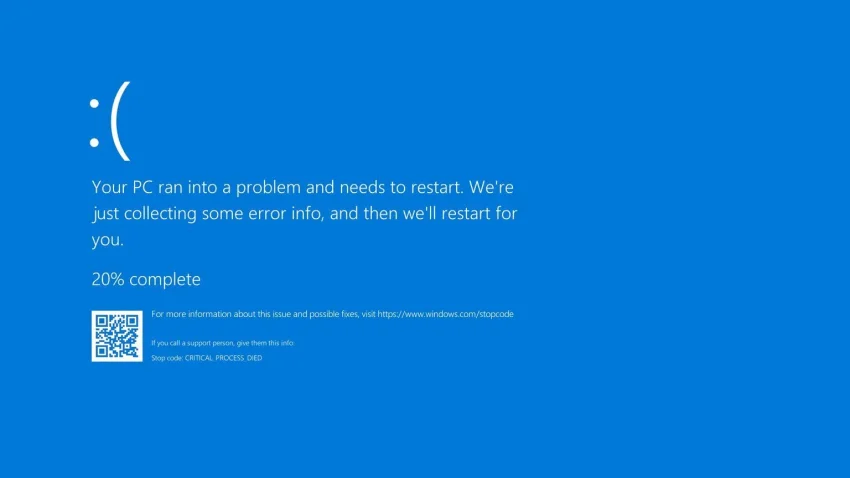
When Trusty Tools Fail: The Saga of Y2CrowdStrike
Hello, my loyal band of cyber sentinels. Today, we’re diving into a topic that’s causing quite the stir in the cybersecurity world: the recent CrowdStrike fiasco, or as I like to call it, Y2CrowdStrike. Now, the Grump CISO typically avoids spotlighting specific products, but this incident is just too significant to ignore. Imagine our digital…
Peering into the Abyss of the Dark Web
Hello my ever-vigilant cyber sentinels. Today, we’re delving into the murky depths of the internet the Dark Web. Just hearing those words is enough to make any CISO’s blood pressure spike. It’s like the seedy underbelly of a medieval marketplace, where anything and everything can be bought and sold, often with nefarious intent. In this…
Fortifying the Digital Frontier: Embracing SASE in Our Remote Work Era
Hello, my trusty cyber sentinels! Today, we embark on a journey into the mysterious and often misunderstood realm of Secure Access Service Edge, or SASE. Now, I know what you’re thinking: “Another acronym to keep track of?” But bear with me, because SASE might just be the key to fortifying our digital fortress in ways…
Securing the Digital Outposts: Remote Work Environments in the Modern Age
Hello, my loyal band of cyber sentinels. Today, we’re tackling a topic that hits close to home for yours truly: securing remote work environments. Now, as the Grumpy CISO who’s been navigating the digital seas from the comfort of my own home office, I can tell you firsthand that this is a subject near and…